Cybersecurity

(Source: kaltoons.com)
Why we need Cybersecurity?
With the rapid expansion of the internet over the last few decades and the technology boom, we find ourselves in an era where we have to depend so much on the internet to get on with our daily activities. Unless you are living in the wild.
Millions of people start their day waking up in the morning to check how many notifications they received on their smartphone or tablet. Invariably it leads to also checking Facebook, Twitter, Instagram, WhatsApp, email, news and even checking the balance on their bank account. This process goes on with individuals as well as businesses that depend on technical devices and networks to connect to different computer networks.
With all these great benefits of modern information technology also comes unprecedented computer security risks to individuals and organisations. It has already proven to be one of the biggest challenges that we face today to protect information in cyberspace.
What is Cybersecurity?
Cybersecurity, also known as Information security is protecting Information Technology i.e. computer systems, networks, data from being attacked, destruction and unauthorised access and from vulnerabilities.
Cyber Risks
The typical and most common cyber security risks we hear about every day are computer viruses, stealing financial data and intellectual property by hacking into web sites, databases and systems, Identity theft, Denial - of service (DoS) attacks carried out by individuals or organised groups.
There are also risks of more sophisticated cyber criminals or organisations that conduct terrorist activities through cyberspace or sabotage and espionage to destroy, damage or extract sensitive information.
Challengers of Cyber security
Most businesses fail to keep up on cybersecurity due to many reasons, lack of well-developed security policies, access control, privilege allocation and lack of education on cyber threats.
Main Goals
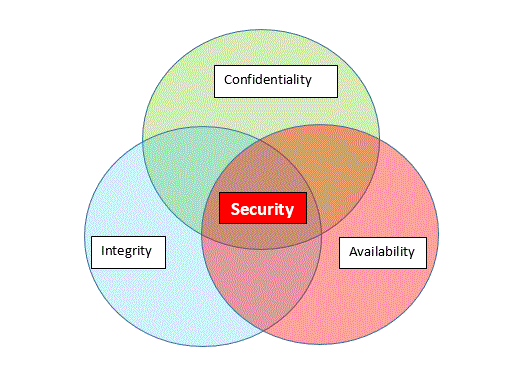
While it’s impossible to completely secure a computer system. The aim is to identify vulnerabilities and to minimise the risks. There are multiple definitions for cybersecurity goals but the main goals of security are maintaining Confidentiality, Integrity and Availability.
Confidentiality is maintaining access to computer systems or assets only to the authorised parties. This can also be referred to as privacy or secrecy
Integrity ensures the computer assets can only be modified by the authorised parties in an authorised way.
Example: securing personal identity data getting changed by hackers.
Availability ensures the computer assets are available and accessible to authorised parties when required. Denial of service (DoS) attacks are the main threat for availability.
A system is most vulnerable at its weakest point and hackers always look for the easiest way in to take control of systems. This is also called the Principle of Easiest Attack. IT security teams must always be on alert, monitor and consider all possible means of system penetration to identify the vulnerabilities and risks to make sure the systems are secure.























